Poison Ivy 3.0.3 with Crypto Currencies Clipper is a type of malware, specifically a variant of the Poison Ivy Remote Access Trojan (RAT) that has been modified to target cryptocurrency users.
Poison Ivy is a well-known Remote Access Trojan (RAT). RATs are malicious programs that allow attackers to remotely control an infected computer, giving them access to files, keystrokes, and other sensitive information. I provide you the Poison lvy RAT Crack Download Link below.

Poison Ivy 3.0.3 with Crypto Currencies Clipper is a sophisticated piece of malware that combines the remote access capabilities of the poison Ivy rat with additional features to steal cryptocurrency by intercepting and modifying transactions.
About Poison lvy With Crypto Stealer – The Best Remote Access Tool
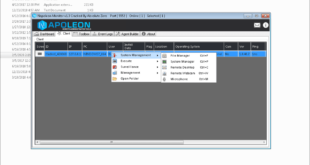
Poison Ivy with Crypto Currencies Clipper is a versatile piece of malware that includes a range of functionalities.
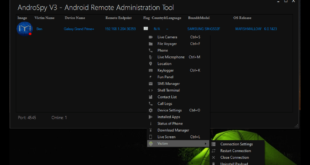
It provides full control over the victim’s desktop environment. The attacker can view and interact with the desktop as if they were physically present, making it possible to manipulate applications and files directly.
Also Check: LuxNET Rat Crack Latest Version
Poison lvy Rat allows monitoring and management of running processes. The attacker can terminate processes that might be interfering with their activities or conceal the malware’s presence.
It facilitates the browsing, copying, moving, and deletion of files. This can be used to exfiltrate sensitive documents or install additional malware.

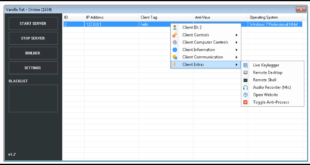
It also intercepts and alters cryptocurrency transaction addresses. By modifying the recipient’s address, the attacker redirects funds to their cryptocurrency wallet, effectively stealing the victim’s cryptocurrency.
It might involve spreading or propagating the malware via torrent networks, or it could be a mechanism for distributing malicious payloads.
It is a powerful tool for data exfiltration. By recording every keystroke, hackers can capture usernames, passwords, and other confidential information, which can be used for identity theft or corporate espionage.

Hackers can use infected machines to launch Distributed Denial of Service (DDoS) attacks against targeted websites or services. This can be done for various reasons, such as extortion, political activism, or to disrupt business operations.
Features
- Remote desktop
- File manager
- Report windows
- Keylogger
- Process manager
- Password recovery
- Webcam
- Bot killer
- Remote shell
- Bitcoin clipper
- Seed torrent
- Ddos attack
- Downloader
- Color
- Visit website
- Get admin privileges
- Disable windows defender
- Blank screen
- Chat
- Send file
- Send file in memory
- Shut down
- Log off
Crack Poison lvy Rat Download Latest Version
Download Link 1

Download 2025 Latest Hacking Softwares & Exploits
Download Link 2

Also Check: Shadow Miner Crack Latest Version
Join Us On Our Telegram For Latest Hacking Software Update
 Black Hat Softwares Download latest hacking programs, malwares, crypters, binders, android rats, windows rat for free.
Black Hat Softwares Download latest hacking programs, malwares, crypters, binders, android rats, windows rat for free.