ICARUS RAT is a remote access trojan (RAT) associated with malicious activity. Like other RATs, it allows an attacker to access and control a victim’s computer.
The icarus rat can facilitate various malicious activities, such as stealing sensitive information, capturing keystrokes, and executing commands on the compromised machine. I have provided you with the Icarus RAT Crack Download Link below.
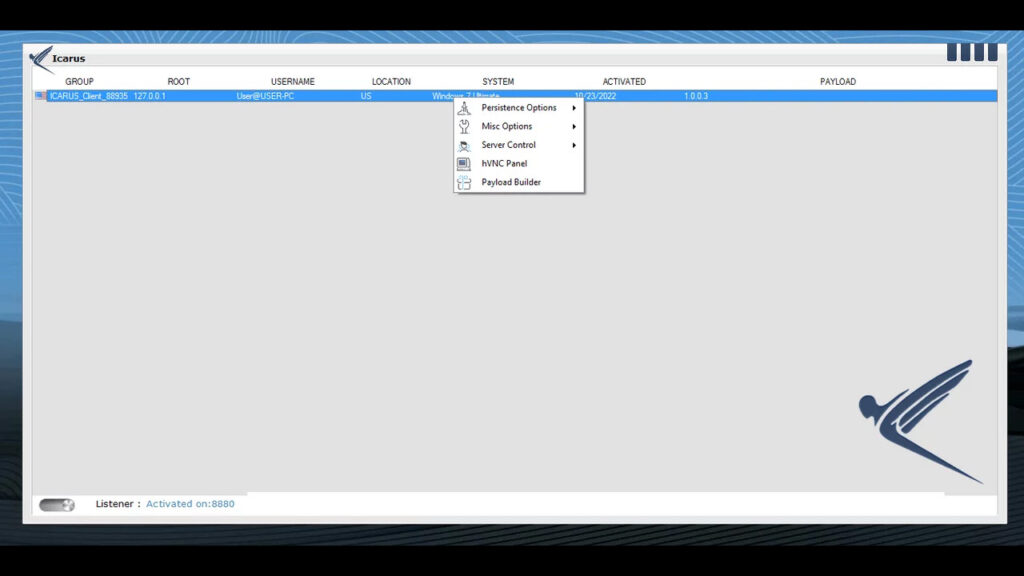
The malware spreads through phishing emails, malicious links, or infected software downloads. Once installed, it can remain hidden, making it challenging for users to detect its presence.
About Icarus RAT – The Best Remote Administration Tool
The icarus rat is a sophisticated remote access trojan designed to give attackers extensive control over compromised systems.
It allows the attacker to control the victim’s computer without displaying any visible signs of the connection. It supports smooth operation, even enabling hidden applications like Discord, and allows the installation of additional malware without the victim’s knowledge.
Also Check: Prynt Stealer Crack Latest Version
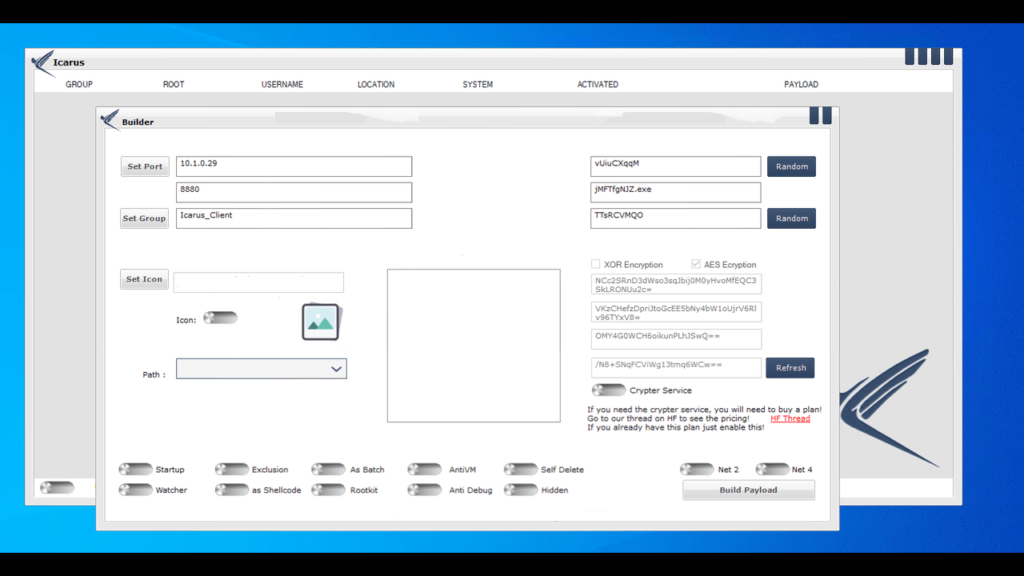
The icarus rat can build a stub (a small program) for different versions of .NET is a notable feature. This makes it harder for users to detect or remove the malware, as it can embed itself deeply into the system.
ICARUS RAT includes tools to steal sensitive information, such as passwords or files from specified directories. The capability to export this data to platforms like Telegram or Discord makes it easy for attackers to access stolen information remotely.
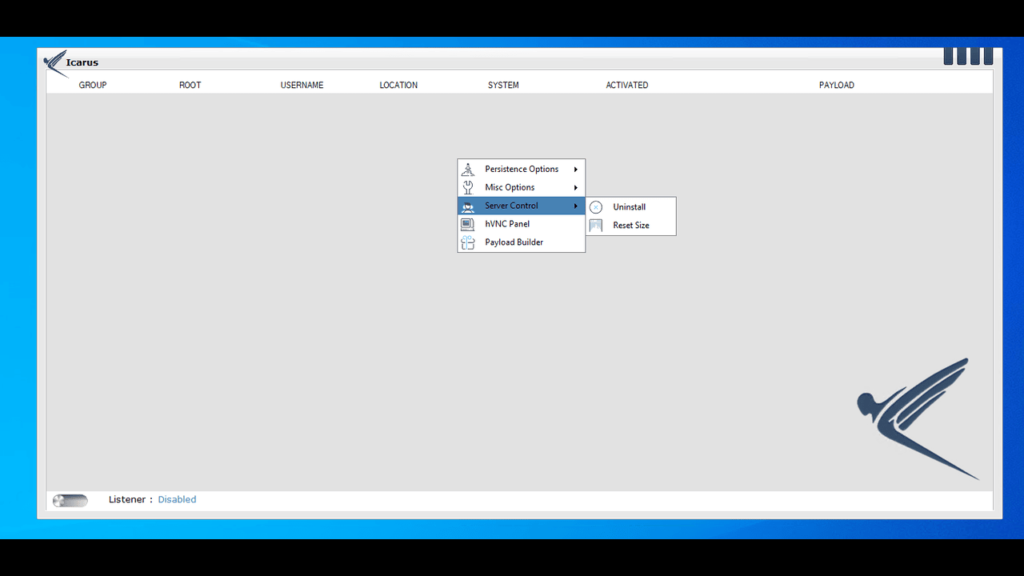
Using icarus rat attackers can interact with applications installed on the victim’s computer without the user being aware, facilitating actions like file manipulation or running commands.
The icarus rat can facilitate the download and installation of other malicious software, such as ransomware or additional trojans, which can further compromise the victim’s system.
By cloning user profiles or gathering personal information, attackers can conduct social engineering attacks, tricking friends or colleagues into divulging more sensitive information.
The rootkit features help attackers maintain a foothold in the system, making it difficult for the victim to detect or remove the rat, thus ensuring continued access over time.
Features
- Hvnc
- Stub creation
- Data theft capabilities
- Profile cloning
- User interface (gui)
- Stealth operation
- Application control
- Customizable stubs
- Rootkit functionality
- Selective data extraction
- Password recovery
- Data exfiltration
- Profile cloning
- Replication of user profiles
- Social engineering
- Surveillance
- Network exploitation
- Installation of additional malware
- Persistence
- Remote control
- Keylogging
- Screen capture
- Persistence mechanisms
- Networked attacks
- Browser integration
- Full control
- File transfer
Crack Icarus Rat Download Latest Version
Download Link 1

Download 2025 Latest Hacking Softwares & Exploits
Download Link 2

Also Check: XWorm Rat Crack Latest Version
Join Us On Our Telegram For Latest Hacking Software Update
 Black Hat Softwares Download latest hacking programs, malwares, crypters, binders, android rats, windows rat for free.
Black Hat Softwares Download latest hacking programs, malwares, crypters, binders, android rats, windows rat for free.