Eagle Monitor is the name of a remote access Trojan (RAT) written in C# and Visual Basic programming languages.
It allows the attackers to remotely control infected computers. Typically, RATs are used to steal sensitive information, inject additional malware, spy on victims, etc. We have discovered Eagle Monitor on a hacker forum. I provide you the Eagle Monitor RAT Crack Download Link below.
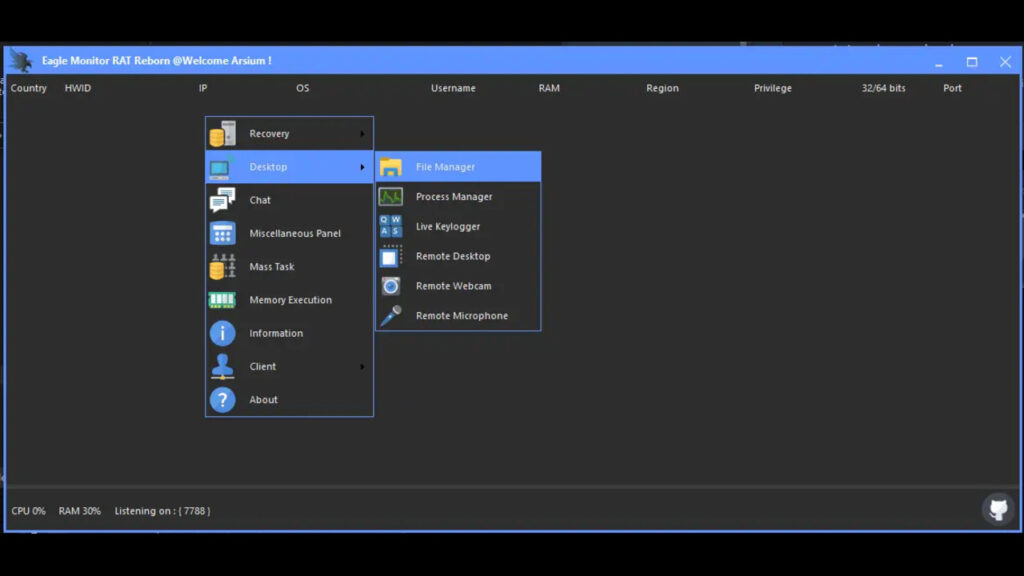
Eagle Monitor can steal usernames, passwords, and browsing history from Google Chrome (and possibly other) browsers. Also, it can download, rename, delete, and execute files stored on the infected computer, and create shortcuts for those files.
About Eagle Monitor RAT – The Best Remote Administration Tool
A Remote Administration Tool is software that gives the attacker full control over the victims’ device remotely. Using RATs, attackers can perform various tasks such as accessing files, cameras, and other resources remotely while conducting keylogging, system operations, etc.
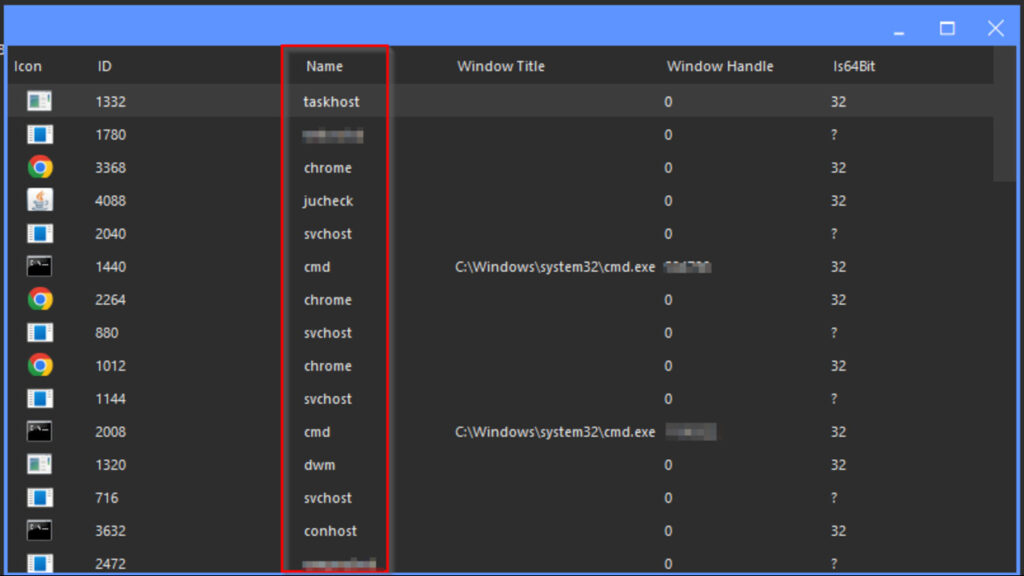
Its process manager feature allows it to kill, suspend, resume, and inject processes (see the running processes’ details).
Also Check: SSH Rat Keylogger Crack Latest Version
Eagle Monitor includes a keystroke logging feature allowing attackers to record keyboard input (gather data entered with the keyboard) in online and offline modes.
Its remote camera and desktop viewer features can capture screenshots and webcam feeds. Another feature available in the EagleMonitor is a shellcode injection that can be used to exploit vulnerable programs.
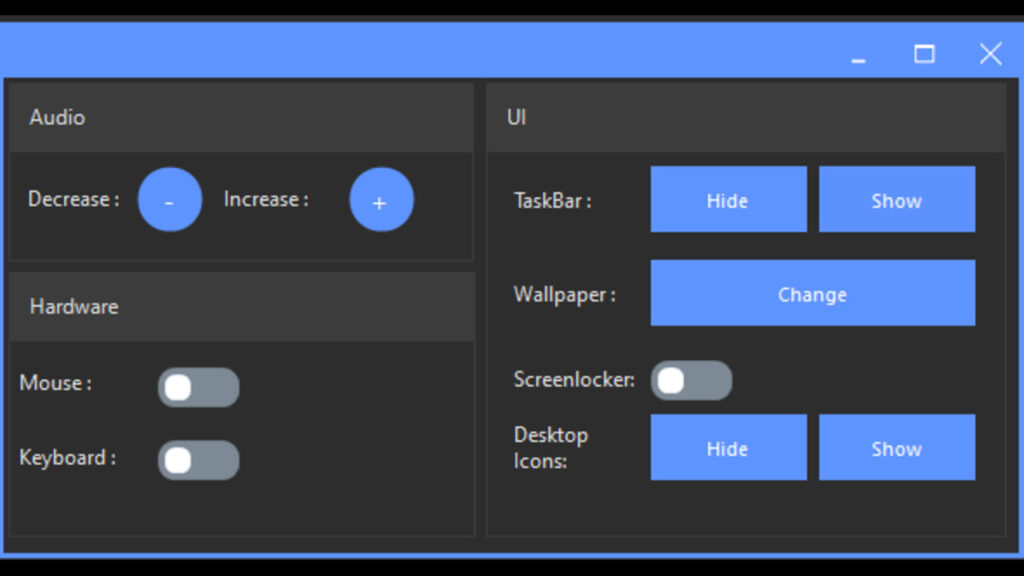
The EagleMonitor can hide (and show) the taskbar, change the wallpaper, increase, and decrease volume, show and hide desktop icons, and get the CPU information.
It can shut down and restart a computer, log out from Windows, launch the BSoD (Blue Screen of Death), lock the screen, etc. Eagle Monitor is quite a powerful RAT allowing threat actors to perform a wide range of actions.
It can steal credit card details, passwords, and plenty of other information, steal files, and more. It seems that it targets mainly information that can be misused to steal identities, personal accounts, and other purposes.
Most attackers use emails, fake updaters, cracked software download pages, and other unreliable sources for downloading files/programs to distribute malware.
Features
- Packets system
- All plugins
- Server-side and packet handling
- Client-side and packet handling
- Native imports
- Settings
- Builder
- Automation tasks
- Mass tasks
- Memory execution
- Asynchronous operations
- Use of threads
- Wifi recovery removed
- Logs system
- Keylogger
- Network information (IPV4)
- Client written both in VB and C#
- An installer for deployment
- Notification sound
- Passwords recovery
- History recovery
- Blur screen locker
- Remote camera viewer
- Remote desktop viewer
- Process manager
- Kill process
- Suspend process
- Resume process
- Shutdown system
- Reboot system
- Suspend system
- Hibernate system
- Log out user
- Bsod
- Lock workstation
- Offline keylogger
- Realtime keylogger
- Managed pe execution
- Unmanaged pe execution
- Managed dll execution
- Unmanaged dll execution
- Shellcode execution
- Audio up
- Audio down
- Hide + show taskbar
- Hide + show desktop icons
- Set wallpaper
- File manager
- Delete file
- Download file
- Rename file
- Shortcuts
- Logs
- Mass tasks
Crack Eagle Monitor Rat Download Latest Version
Download Link 1

Download 2025 Latest Hacking Softwares & Exploits
Download Link 2

Also Check: Syria Pro Rat Crack Latest Version
Join Us On Our Telegram For Latest Hacking Software Update
 Black Hat Softwares Download latest hacking programs, malwares, crypters, binders, android rats, windows rat for free.
Black Hat Softwares Download latest hacking programs, malwares, crypters, binders, android rats, windows rat for free.